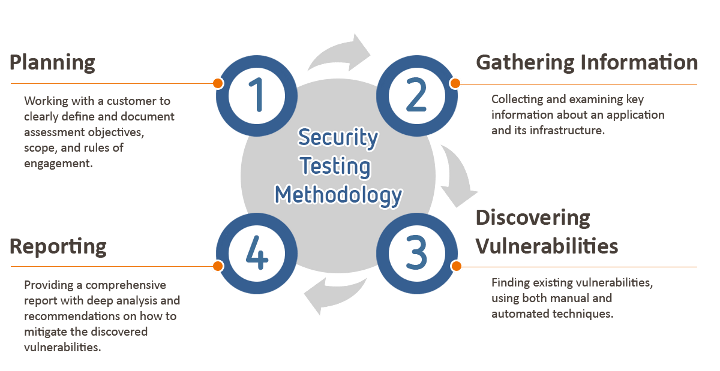
Process of penetration testing in network
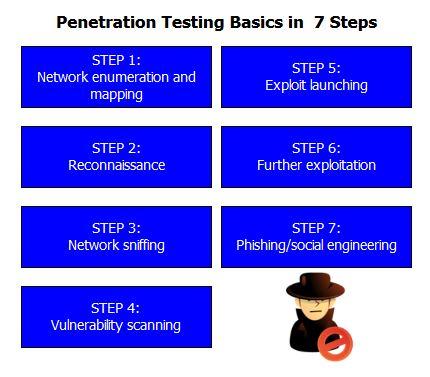

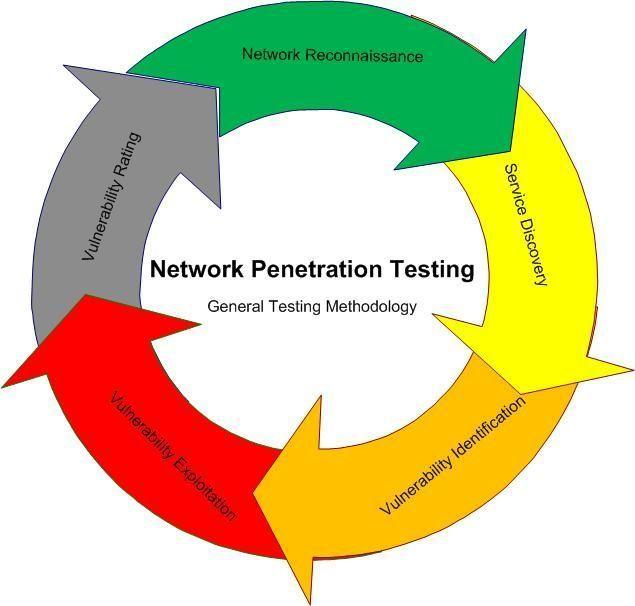

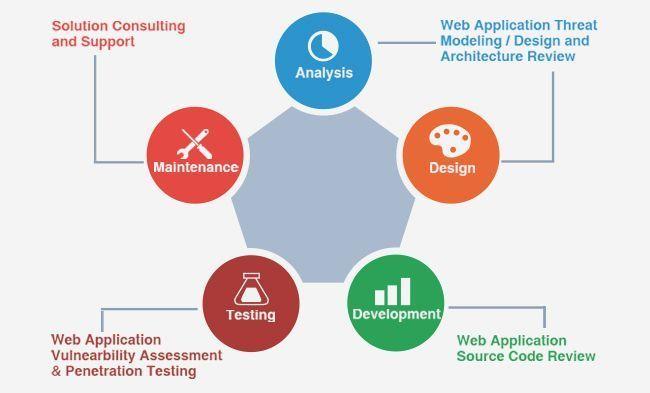


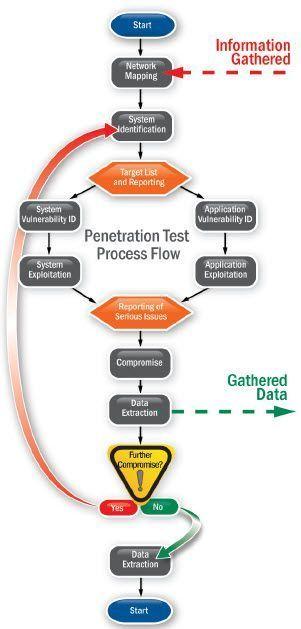


Why Network Penetration Testing?
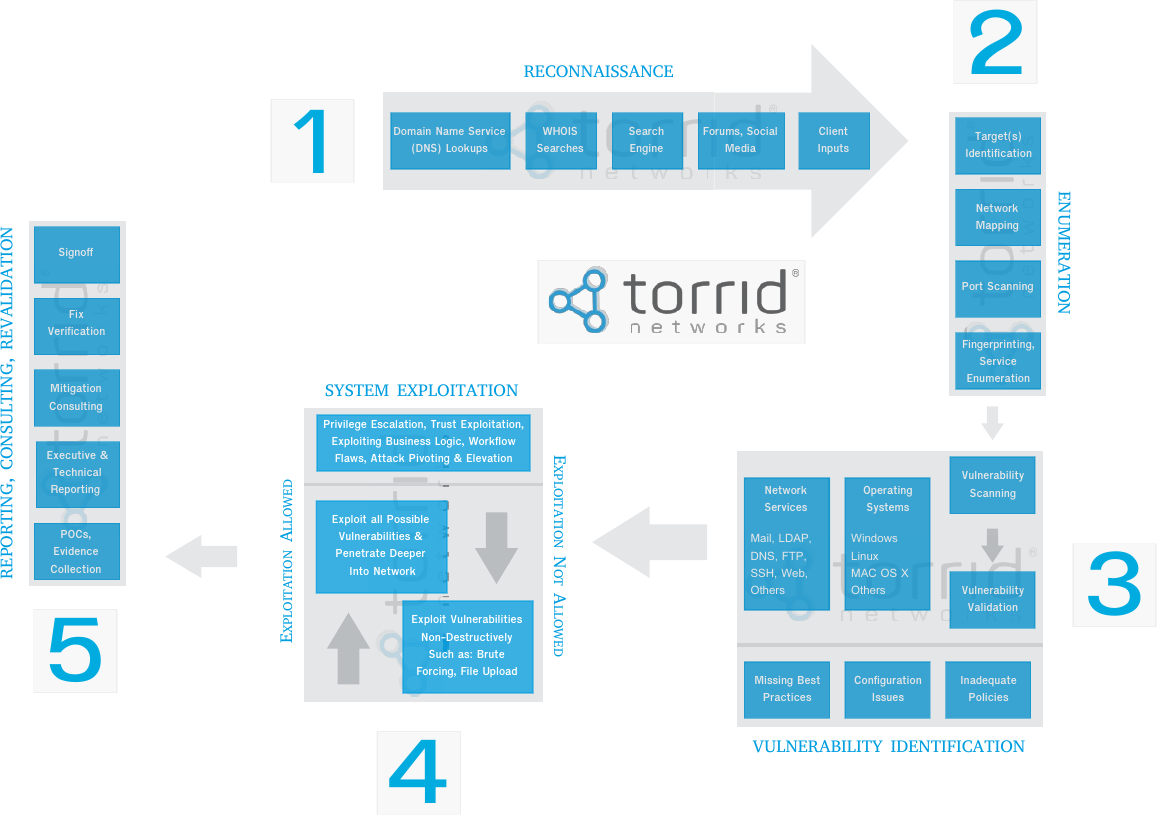


Pre-Test Stage
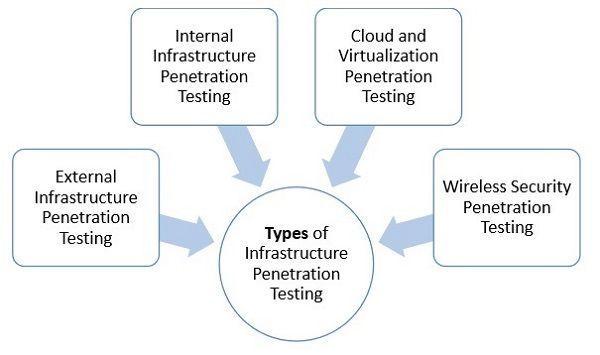

The pen testing process can be broken down into five stages. Gathering intelligence (e.g., network and domain names, mail server) to better understand how a.
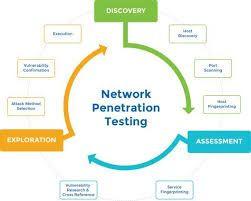
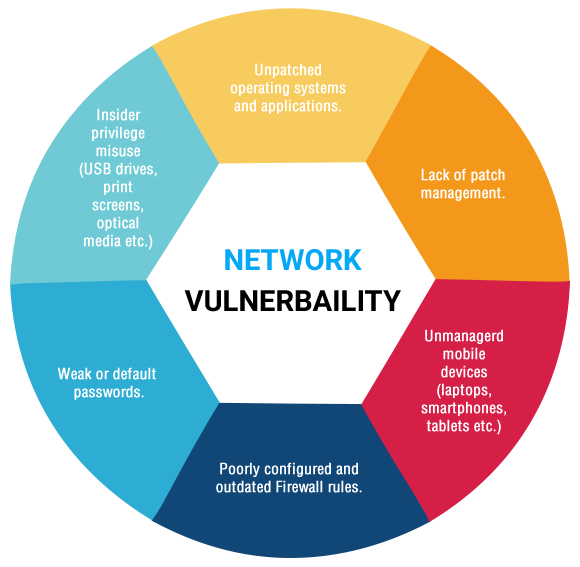

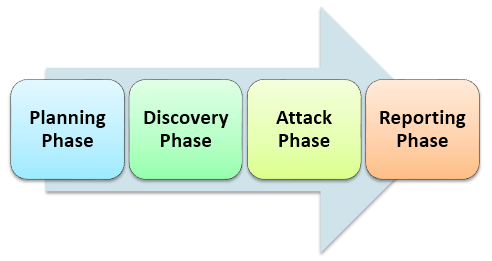

Description:A pen-tester will reveal how newly discovered threats or emerging vulnerabilities may potentially be assailed by attackers. Automated scanning tools, such as Nessus, quickly cover a lot of ground but produce a high degree of false positives and false negatives vulnerabilities are falsely identified or unidentified at all. It has a built-in sniffer, DNS server and access point to mount and facilitate attacks. Regardless of the penetration testing type , state the number of networks, the range of IP addresses within one network, subnets, and computers to avoid any misunderstanding. No matter the reasons for penetration testing, it is useful to become pentest-savvy to assess the vendor before and after the penetration testing. The detailed reports that pen-tests generate can help organizations avoid significant fines for non-compliance and allow them to illustrate ongoing due diligence in to assessors by maintaining required security controls to auditors. This kind of test is useful for estimating how much damage a disgruntled employee could cause.

































User Comments 1
Post a comment
Comment: